Trusted, Interoperable Cybersecurity Data Space
Creating a comprehensive platform for collecting, recording, sharing and analyzing cyber incident information between public, private and research organizations across Europe and beyond.
The Cybersecurity Crisis
Europe faces an unprecedented surge in cyberattacks with devastating financial and reputational consequences
46.5%
EU countries targeted in H1 2023
Growth from 9.8%
to 46.5%
Source: ENISA Financial Threat Landscape 2024
$15.6T
Expected global cost by 2029
Scalability Crisis
Increasing incidents need systematic approach
Poor Coordination
Lack of coordination between market players
Fragmented Data
Closed or fragmented incident data
Slow Response
Delayed response to emerging threats
Our Comprehensive Solution
A SaaS platform serving as Trust Anchor in the Cybersecurity Data Space ecosystem
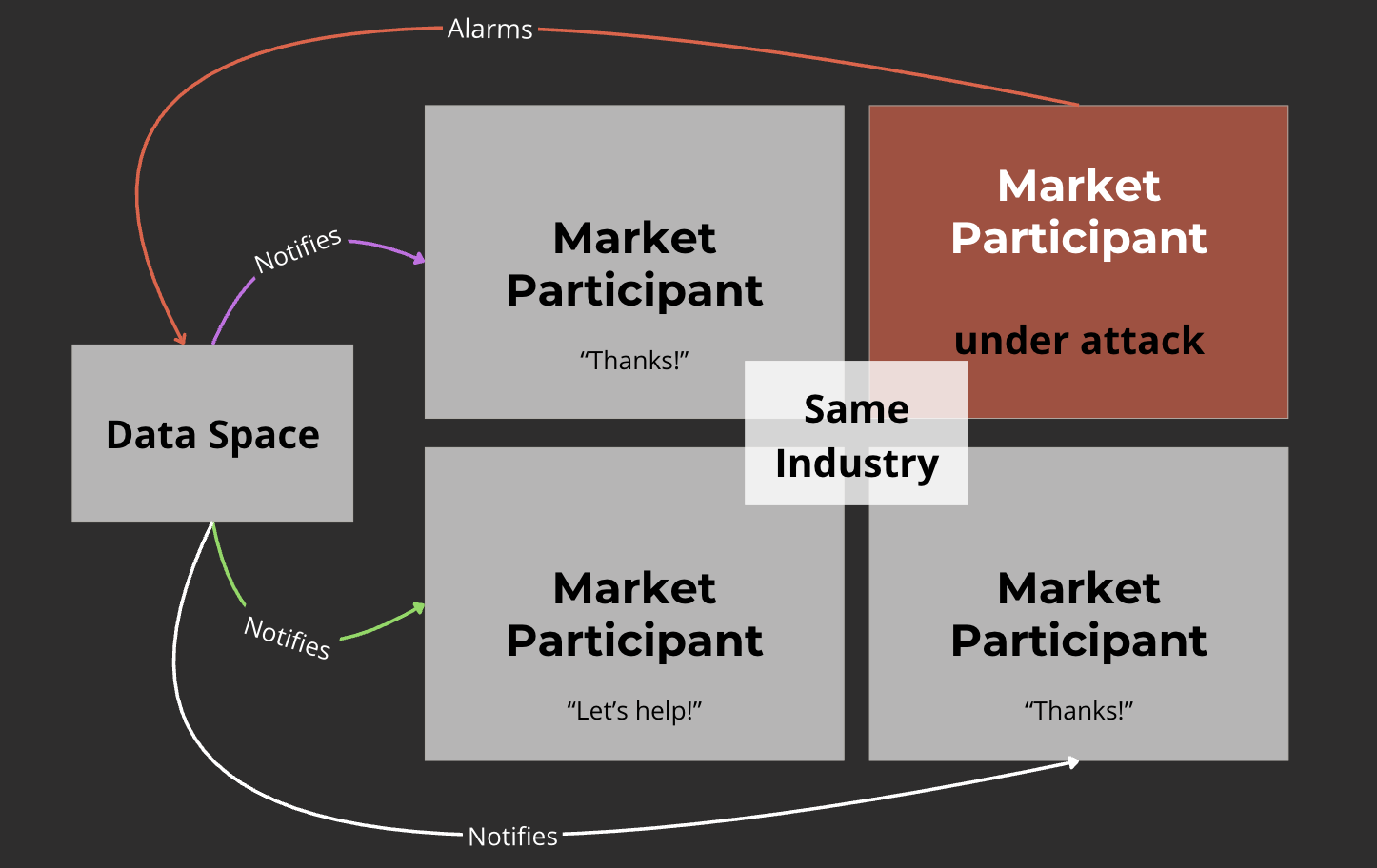
Organization Registration
User registers organization as Data Provider in the system
Incident Submission
Submit incident in STIX 2.1 format, fully compatible with NGSI-LD
Processing & Classification
System processes, classifies, anonymizes and notifies related parties
Blockchain Recording
Data hashed and recorded on Solana blockchain, NFT created with metadata, reporters have public proof of reporting on time.
Powered by FIWARE
Built on Europe's leading open-source platform for smart solutions, ensuring interoperability, scalability, and compliance with European digital standards.
Real-time context information management for cyber incident data
- • NGSI-LD API compliance
- • Real-time data synchronization
- • Unification of the reporting data model
- • Subcription to threat alarms
Secure authentication and authorization for all participants
- • OAuth 2.0 & OpenID Connect
- • Role-based access control to sensitive data
FIWARE Integration Benefits
Secured by Blockchain
Leveraging Solana's high-performance blockchain for immutable incident records, ensuring data integrity and creating verifiable audit trails.
High-speed, low-cost blockchain for incident data hashing
- • 65,000+ transactions per second
- • Sub-second finality
- • Minimal transaction costs
- • Energy-efficient consensus
Secure smart contract development for data integrity
- • Type-safe smart contracts
- • Automated security checks
- • Rust-based development
- • Built-in testing framework
NFT metadata for incident report verification
- • Immutable metadata storage
- • Verifiable incident records
- • Automated NFT creation
- • Cross-platform compatibility
Blockchain Implementation
Data Integrity Process
Key Benefits
Complete Technology Stack
European data exchange standards with guaranteed data sovereignty
- • Data sovereignty compliance
- • Federated data spaces
- • Trust framework integration
Automatic detection of anomalies, trends, and potential threats
- • Pattern recognition
- • Predictive analytics
- • Threat intelligence
User-friendly dashboards for analytics, statistics, and reporting
- • Real-time dashboards
- • Custom reporting
- • Interactive analytics
Unified system for authentication and policy-based access
- • Multi-factor authentication
- • Role-based permissions
- • Audit logging
Industry-standard format fully compatible with NGSI-LD
- • Structured threat information
- • Interoperability standard
- • Machine-readable format
Selected participants get different access permissions to data
- • Granular access control
- • Data classification levels
- • Participant verification
Target Audience & Participants
Critical Infrastructure Operators
Essential services and infrastructure providers
- • Energy sector operators
- • Transportation networks
- • Financial institutions
- • Healthcare systems
IT Companies
Technology service providers and software companies
- • Managed service providers
- • Software development firms
- • Cloud service providers
- • Cybersecurity vendors
State Authorities
Government agencies and regulatory bodies
- • CERT organizations
- • SSSCIP (State Service)
- • SSU (Security Service)
- • Cyber police units
Incident Response Centers
Specialized cybersecurity response teams
- • National CERTs
- • Sectoral response teams
- • Private incident responders
- • International cooperation bodies
Universities & Research
Academic and research institutions
- • Cybersecurity research labs
- • Academic institutions
- • Think tanks
- • Innovation centers
International Organizations
Cross-border cooperation entities
- • ENISA
- • EU agencies
- • NATO cyber centers
- • Regional partnerships
Business Model & Traction
€500
per year subscription
1,000
target clients
€500K ARR
€100K
GovTech procurement
5
government bodies
€500K ARR
TBD
3rd party providers
∞
scalable revenue
Growth
€+
Grants & collaborative R&D
EU
funding programs
Support
€2M
Project Valuation
€200K
Pre-seed round
10% allocation (SAFT)
Strategic Opportunities
Cooperation with leading European digital initiatives
Unique position in the global cybersecurity landscape
Perfect window for European digital infrastructure integration
Leadership Team

Kyrylo Gorokhovskiy
Chief Executive Officer
Strategic leadership and business development expertise. Driving partnerships with European digital initiatives and government relations for cybersecurity data space implementation.

Ivan Volkov
Chief Technology Officer
Technical architecture and platform development leadership. Expert in FIWARE, blockchain technologies, and European data space standards implementation.

Ivan Lysenko
Cybersecurity Analyst
Threat analysis and security expertise. Specializing in incident classification, STIX 2.1 format implementation, and cybersecurity intelligence analysis.
Get In Touch
Ready to Secure Europe's Cyber Future?
Join the revolution in cybersecurity data sharing. Whether you're an organization looking to enhance your incident reporting capabilities, a regulator seeking better oversight, or an investor interested in the future of European cybersecurity infrastructure.
